Quantum computers are powerful machines capable of solving complex equations much faster than ordinary computers. Some experts estimate that they could crack encryption in minutes that would take today’s fastest computers thousands of years to crack. What impact will this have on the financial system? What about energy and nuclear systems?
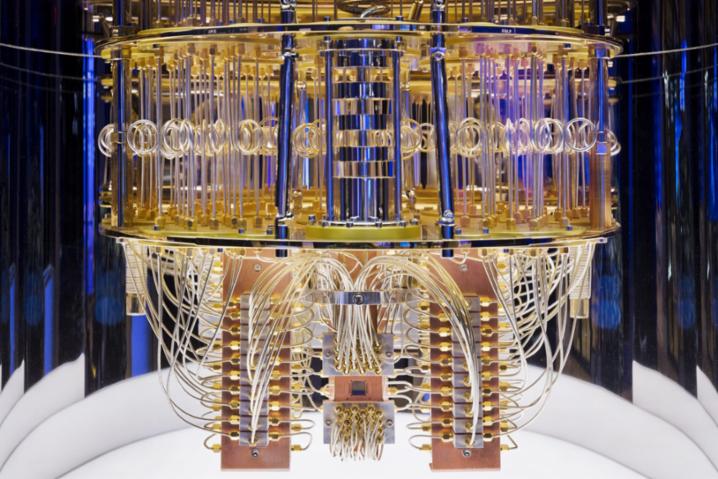
The world’s most powerful supercomputers would take thousands of years to mathematically solve modern Advanced Encryption Standard (AES) or RSA encryption algorithms.
Quantum computers: how do they work?
A quantum computer is not really a “computer” as such, but rather a supercomputer, capable of executing certain powerful algorithms much faster than an ordinary processor. And it does so using the principles of quantum mechanics. Such systems implement quantum bits (“qubits”), two-state quantum systems.
Unlike conventional computers, which encode information in binary form, qubits are not limited to “0” and “1”, but can be in any combination (or “superposition”) of the two. This multiplication, combined with the fact that N qubits can also be combined or “entangled” to represent states simultaneously, means that calculations can be carried out in parallel, opening up an immense field of possibilities.
Nor do quantum computers resemble their classical counterparts. Current models look more like large cans suspended from the ceiling, cooled to near absolute zero (-273.14°C), with hundreds of cables dangling from them.
Anyone wishing to build a quantum computer today must first overcome the fact that qubits are extremely fragile and difficult to stabilize.
In November 2002, IBM unveiled the world’s largest quantum computer, with 433 qubits. With 1000-qubit quantum computers, known as noisy intermediate quantum computers (NISQs), we can already see valuable practical applications in materials design, drug discovery or logistics. Google has its own plan to build a million-qubit quantum computer by 2029.
Managing the threat of quantum cybersecurity
The “quantum threat” posed by quantum computing. As mentioned in the previous section, integer factorization is one type of problem that quantum computers can solve particularly effectively. Most of our digital infrastructure and, fundamentally, everything we do online – from video conferencing to sending e-mails to accessing our online bank account – is encrypted using cryptographic protocols based on the difficulty of solving this type of integer factorization problem.
Current cryptography relies on difficult mathematical problems, such as integer factorization and discrete logarithms, which would take our current computers a long time to solve. However, a quantum computer of sufficient size can accelerate the solution of these problems so significantly that it will effectively break the cryptographic algorithms currently in use.
These advances in computing capacity will threaten cryptographic algorithms whose security relies on mathematical complexity. This means that some forms of cryptography, such as public-key cryptography, are likely to be decrypted by quantum computers. This means that organizations need to rethink the way they use cryptography to ensure that online transactions are secure,
According to an article in Nature, a team of Chinese researchers has unveiled a technique that, in theory, could break the most common methods used to guarantee digital privacy, using a rudimentary quantum computer.
La cryptographie quantique
Bien qu’il n’en soit encore qu’à ses balbutiements, le chiffrement quantique a le potentiel de devenir un mécanisme bien plus sécurisé que les autres types d’algorithmes cryptographiques qui l’ont précédé. Et en théorie, il est même impossible à pirater. Contrairement à la cryptographie traditionnelle, qui repose sur les mathématiques, la cryptographie quantique repose sur les lois de la physique.
According to the National Institute of Standards and Technology (NIST), post-quantum cryptography (PQC) aims to “develop cryptographic systems that are secure against both quantum and classical computers, and that can interoperate with existing communication protocols and networks”.
Not to be confused with quantum cryptography, which relies on the natural laws of physics to produce secure cryptosystems, post-quantum cryptographic algorithms use different types of cryptography to create quantum-proof security.
Although this question may seem relatively straightforward, it is not. Not only does the transition to quantum-secure cryptography (also known as post-quantum cryptography, PQC Post-Quantum Cryptography) take years, but scientists don’t know exactly when quantum computers will be powerful and stable enough to decrypt public-key cryptography. Cybersecurity leaders are therefore faced with a dilemma: should I invest now in a threat that has yet to materialize?
This ambiguity over timing is exacerbated by the fact that attackers are already harvesting data today with a view to decrypting it later, when quantum computers are sufficiently mature, in so-called “Harvest-now, Decrypt-later” attacks.